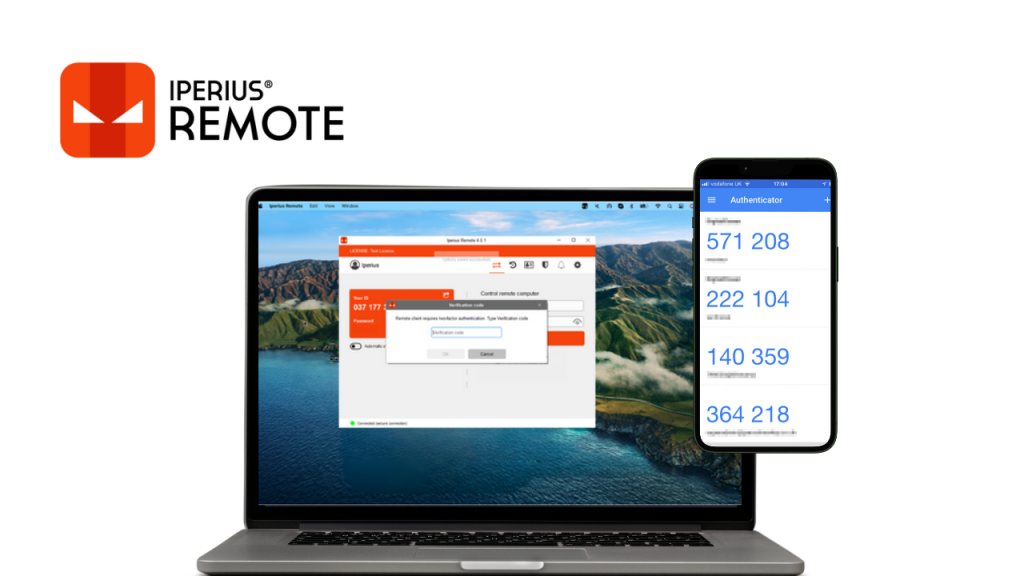
The introduction of two-factor authentication in version 4.5.2 of Iperius Remote marks an important step forward in strengthening security.
This new level of protection is essential in today’s digital landscape, where the frequency and sophistication of cyber-attacks are constantly increasing.
2FA requires users to confirm their identity using two different verification methods, a strategy that dramatically reduces the likelihood of unauthorized access.
Summary:
How 2FA works in Iperius Remote
- Combination of Credentials for Double Security: 2FA in Iperius Remote requires two types of verification: something the user knows (such as a password or PIN) and something the user possesses (for example, a code generated by an authentication app on your smartphone). This combination creates an effective barrier against unauthorized access, even if one of the two credentials were to be compromised.
- Integration with Authentication Apps: Iperius Remote 4.5.2 works in synergy with the main authentication apps, such as Google Authenticator or Microsoft Authenticator, allowing the generation of temporary security codes. This makes the process simple and safe for the user.
Benefits of 2FA in Business Environment
- Protection from Phishing and Other Attacks: 2FA is particularly effective at thwarting phishing attacks and other fraudulent methods aimed at stealing login credentials. Even if a user were to be tricked into revealing their password, the second authentication factor represents a significant barrier to unauthorized access.
- Compliance with Security Regulations: By implementing 2FA, businesses can ensure they comply with various data protection regulations, such as the GDPR. This feature helps prevent data breaches that can lead to heavy fines and reputational damage.
- Peace of mind for Users and IT Managers: The integration of 2FA in Iperius Remote guarantees increased peace of mind, both for end users and IT managers. On the one hand, users have the peace of mind that their data and devices are effectively protected, eliminating concerns about the security of their information. On the other hand, IT managers enjoy a higher level of security, which translates into less need to intervene on potential cyber threats. This proactive approach to security allows you to manage IT resources with greater efficiency and peace of mind.
Conclusion
The integration of two-factor authentication (2FA) in Iperius Remote 4.5.2 represents a decisive step towards strengthened cybersecurity. This functionality not only raises the level of protection against unauthorized access but also reflects Iperius Remote’s commitment to ensuring that its solutions remain in step with the security needs in an ever-evolving digital world.
Improve Security Now!
Find out more about Iperius Remote 4.5.2 and implement two-factor authentication in your company today. Visit our website to get started.

PLEASE NOTE: if you need technical support or have any sales or technical question, don't use comments. Instead open a TICKET here: https://www.iperiusbackup.com/contact.aspx
**********************************************************************************
PLEASE NOTE: if you need technical support or have any sales or technical question, don't use comments. Instead open a TICKET here: https://www.iperiusbackup.com/contact.aspx
*****************************************