BitLocker is a drive encryption system integrated with the Microsoft Windows operating system starting with Windows Vista. It allows you to encrypt hard drives, removable disks or partitions in order to protect them using a specific password and making them inaccessible to third parties. The protection can also be configured for removable drives or USB sticks.
There are also third-party tools for encrypting disks and partitions, such as TrueCrypt or VeraCrypt (considered the best alternative), which are also free. However, they do not give the security in terms of standards and reliability over time that the integrated Windows tool does. BitLocker protects the data on the computer even from theft, since access to the files on the disks will not be possible without knowing the password.
To activate BitLocker in Windows 10 there are different operating modes. One of these requires a motherboard with a chip called TPM (Trusted Platform Module) version 1.2. This chip is used to store security passwords. The fact that passwords are saved on a physical medium, different from the encrypted disk, guarantees considerable security. However it is possible to activate and use BitLocker even on computers without the TPM chip, as we will see later, although this solution may be less secure than the previous one.
How to enable BitLocker to protect data on a partition:
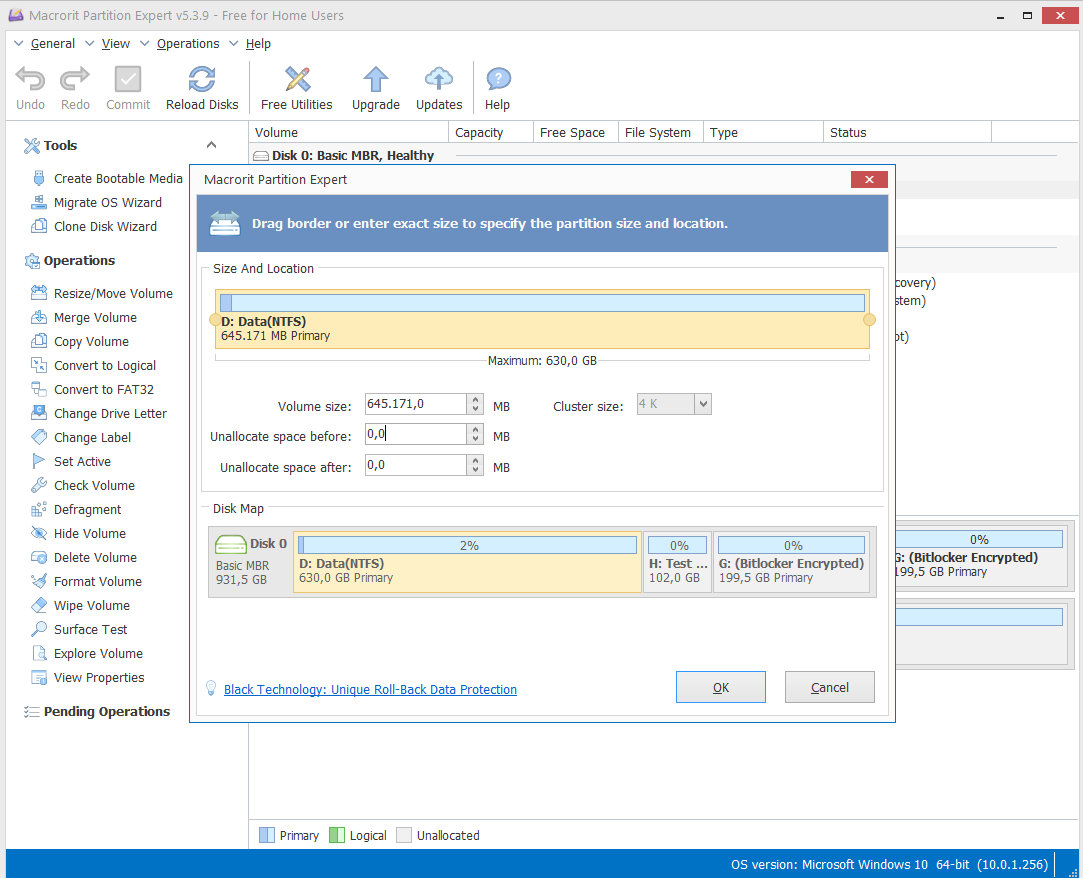
In our example we show how to activate BitLocker on a single disk partition (which can be useful for protecting specific files or programs). Here we use the free “Macrorit Partition Expert” software, but we can use any other freeware software to create partitions. Select a partition and with the right mouse button click on “Move / Resize”. Remove 100 GB from an existing partition:
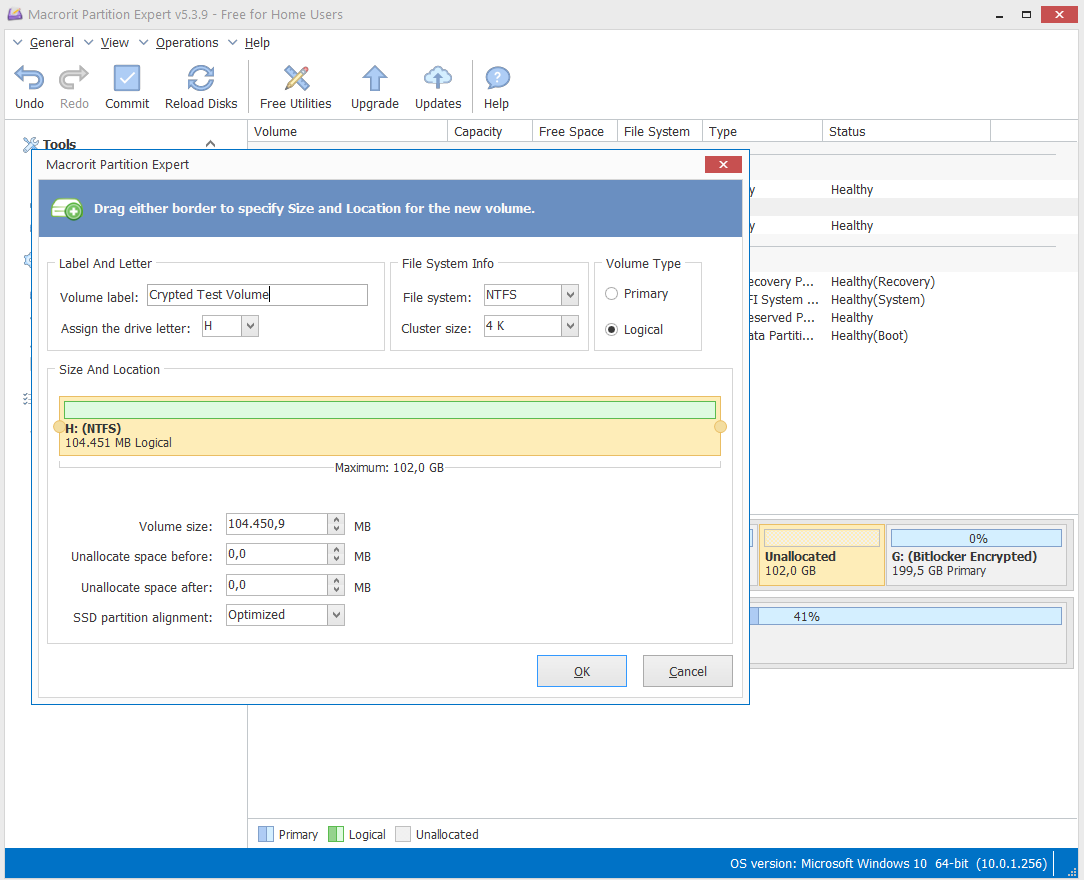
Create the new partition by assigning a file system, a label and a Drive Letter:
By clicking on “Apply” in the toolbar, the software will create the new partition. If you create the new partition on the disk where the Operating System is installed, you must restart the machine.
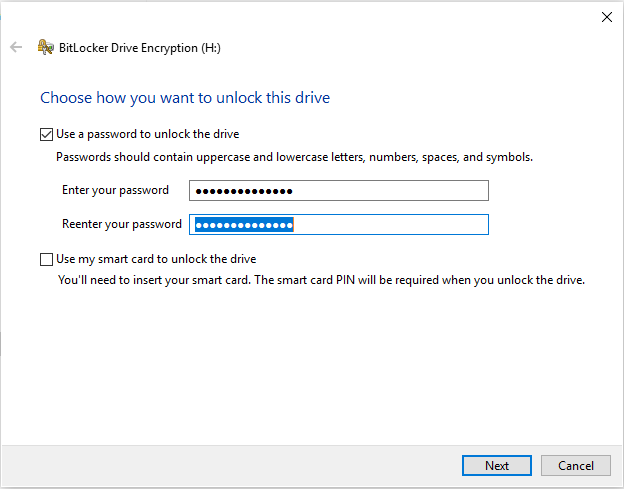
At this point just right-click on the new unit and select “Activate Bitlocker”, a form will appear to choose the mode with which to protect the data. In our example we have chosen the “Password” mode:
After setting the password and clicking on “Next”, BitLocker asks you to choose the password recovery mode.
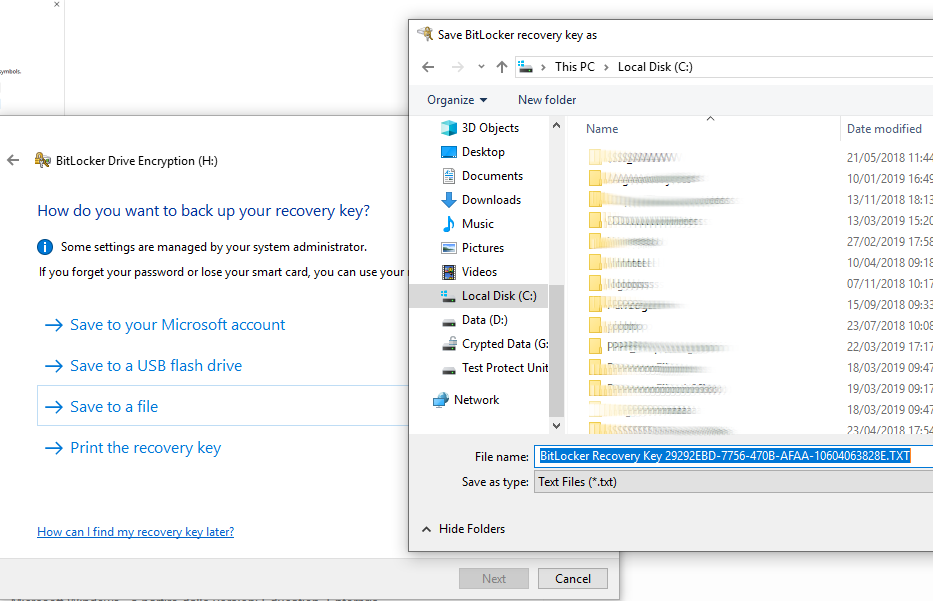
The recovery options include:
- Microsoft Account
- USB flash drive
- File
In the current example we choose to save the Recovery key to a file. For obvious security reasons, the file should be moved from the PC and stored on another device.
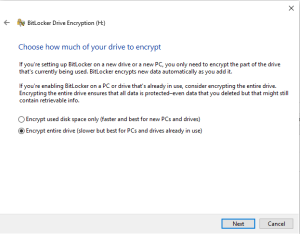
Then BitLocker lets you choose whether to encrypt the entire unit or just the data in it. We choose to protect the entire unit.
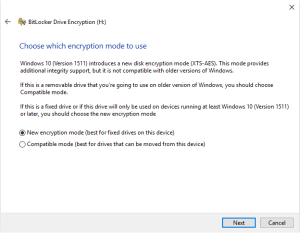
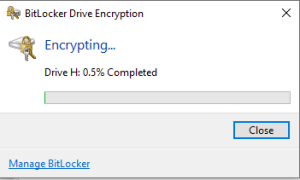
Select “New Encryption mode”, then click “Next” and then click on “Start Encryption”. BitLocker will begin the drive encryption process.
By encrypting the entire disk, the process will be slower.
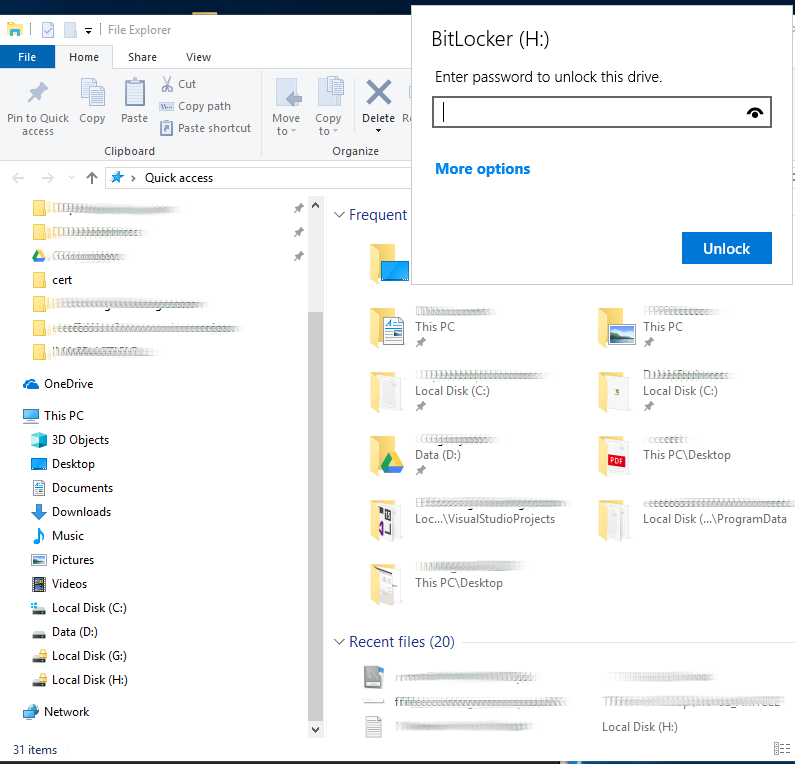
After the process is complete, the disk drive icon will be marked with a yellow padlock to indicate that the disk must be unlocked before being used.
To unlock it just click on it and enter the password that is requested.
Use BitLocker even on computers without a TPM chip
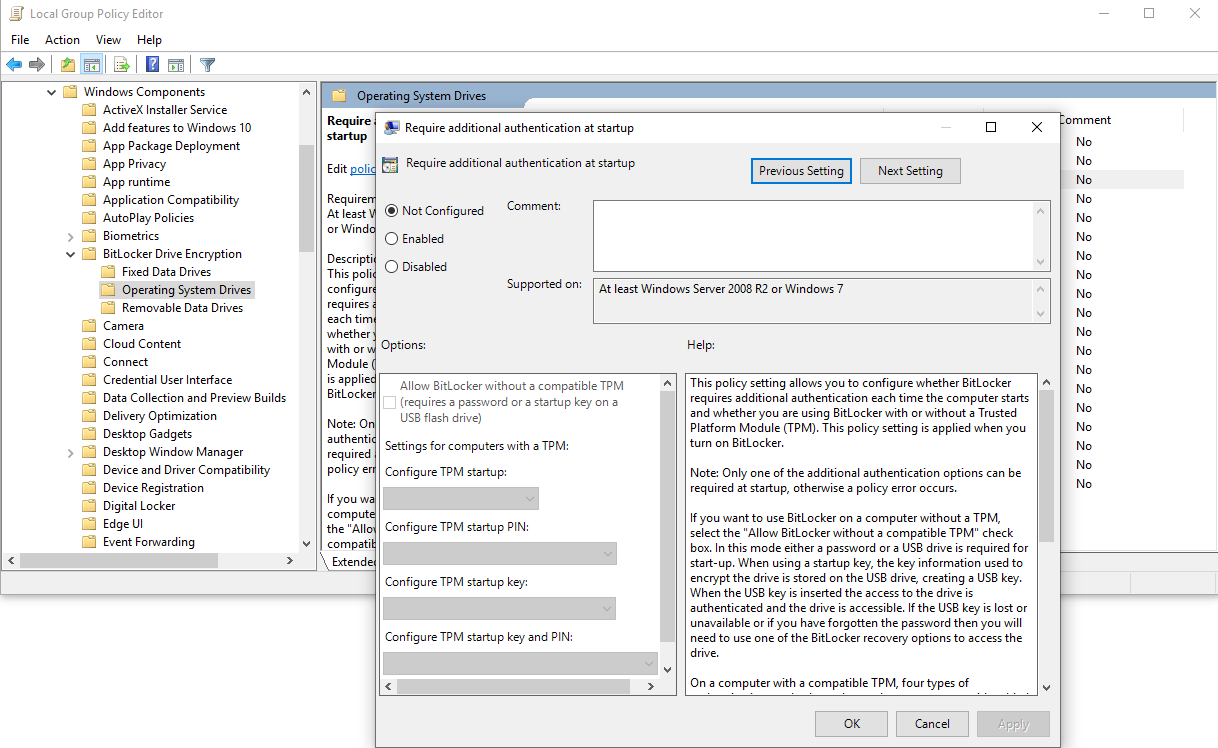
In order to use BitLocker protection on computers without a TPM chip, it is necessary to act on system policies. With this mode, the protection is at the software level, therefore less effective than the chip hardware protection.
By activating the protection and checking the “Allow BitLocker without a compatible TPM” option, we will be able to set an access password or choose to save the credentials on a USB stick. Access to the data will be guaranteed by entering the password each time or by inserting a USB stick when the PC boots up.
Using BitLocker to encrypt a disk drive or partition is a highly recommended practice for protecting sensitive data, both from a HIPAA perspective or simply to avoid credential theft.
Use cases:
Use BitLocker to protect Remote Desktop Connection Manager (RDCMan) data
Remote Desktop Connection Manager is a free utility developed by Microsoft, widely used by network administrators, which allows you to manage multiple Remote desktop connections in a single user interface.
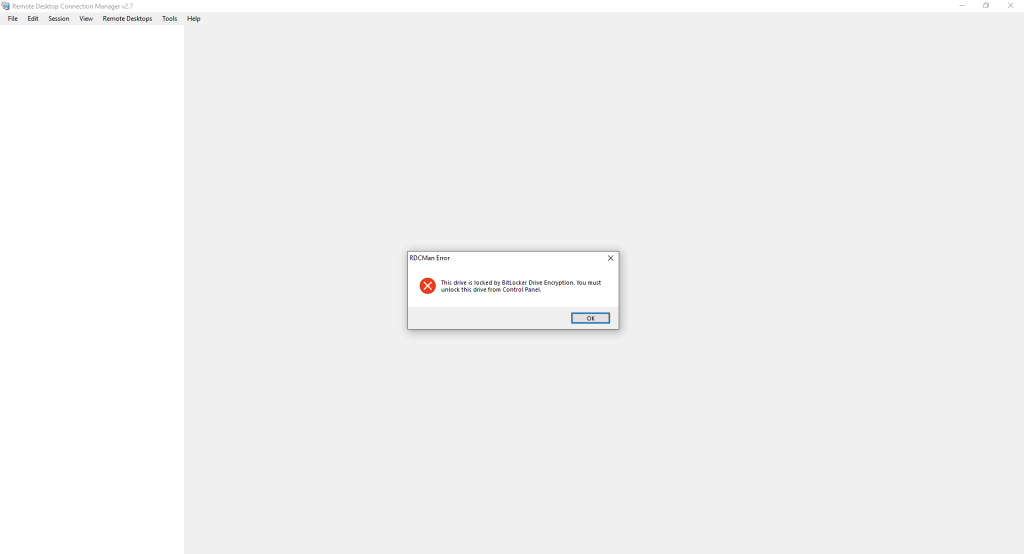
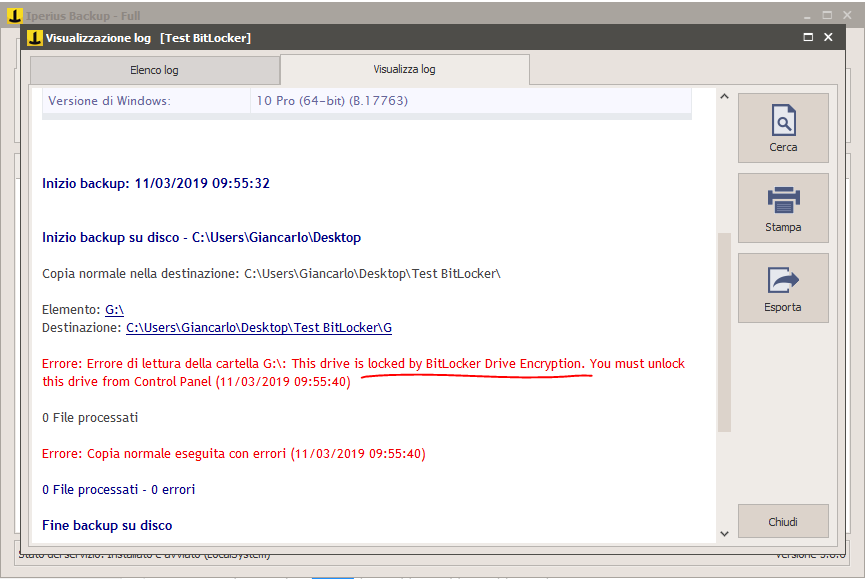
RDCMan allows you to save groups and server objects to connect to. It is also possible to save the login credentials to avoid typing them at every connection. However, the RDCMan archive files that contain the credentials are saved on the disk and, considering that Microsoft has not provided the utility of a “Master Password” feature, any attacker who has access to the computer can easily connect to remote machines simply by opening RDCMan. Using BitBlocker with the protection of a disk drive dedicated to saving Remote Desktop Connection Manager (RDCMan) files can be considered an obligatory method to protect connection data from unauthorized access. The following is the error of RDCMan when trying to access its files, protected inside an encrypted drive:
Use Iperius to back up folders and files from a BitLocker-protected disk:
Data protection with BitLocker also prevents access to backup software that intends to copy files from a protected disk. This obviously also applies to Iperius Backup. If you do not remove the protection from the drive, Iperius will show the following error in the backup logs.
Obviously, by unlocking the disk drive, the backup will run successfully, but this poses some problems when we need to perform automatic backups since unblocking the disk requires explicit user intervention. One solution is to run a script with Iperius before the backup (we can configure it in the backup operation options, “Other processes” panel), where we can insert a command that unlocks the drive before backup, as in the following example:
manage-bde -unlock D: -RecoveryPassword LA-TUA-RECOVERY-KEY
Then, at the end of the backup, Iperius can execute another script that locks the drive again:
manage-bde -lock D:
However, it is pointless to add how unsafe it is to keep a script on a disk with a clear password to decrypt the BitLocker protected disk. A safer way to back up hard drives encrypted with BitLocker is to use the Drive Image backup mode.
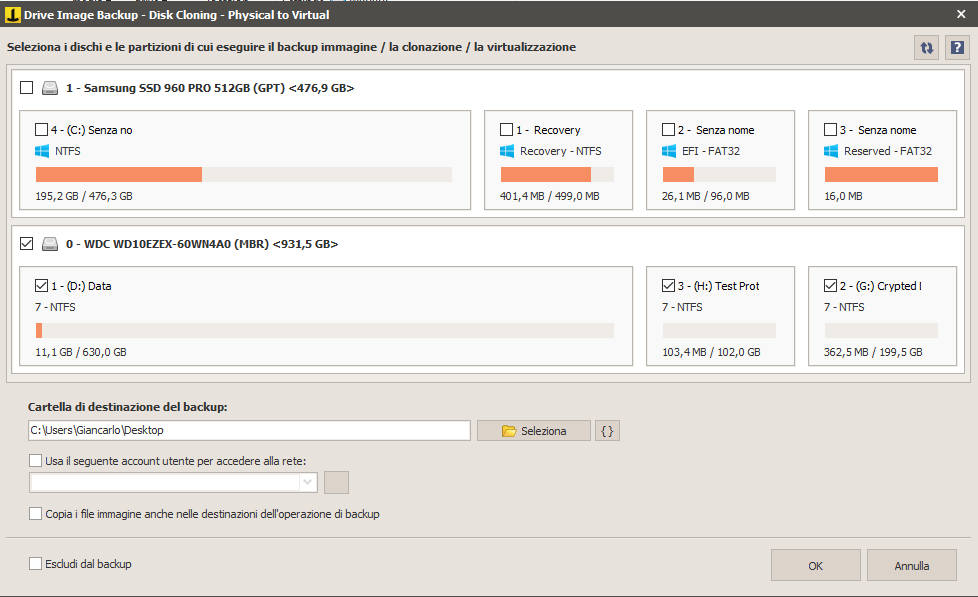
Drive Image Backup with Iperius of a disk drive protected with BitLocker:
Another scenario we find in Iperius Drive Image Backup. The backup is performed successfully both in the case of a locked drive and in the case of an unlocked drive. Subsequently, when “.vhdx” image file is eventually restored, if the drive was locked at the origin it will be restored with the active lock, vice versa will be restored unlocked:
Iperius can, therefore, be considered an excellent software to clone a hard disk or SSD with BitLocker. Furthermore, Iperius allows you to restore a BitLocker encrypted disk, following the procedure shown in the following tutorial: Restore a BitLocker Drive Image Backup with Iperius Recovery Enviroment®
See also: Drive Image Backup, P2V and Disk Cloning with Iperius
The same thing will happen if you run a Windows Drive Image (the drive image compatible with Windows Backup that Iperius runs via the wbadmin interface). This actually attracted some criticism, given that the Windows backup system explicitly warns that the disk backup will not be encrypted in turn. However, security can be guaranteed by saving the backup, ie the VHDX image file, on a path which is itself encrypted or otherwise inaccessible except through authentication.

PLEASE NOTE: if you need technical support or have any sales or technical question, don't use comments. Instead open a TICKET here: https://www.iperiusbackup.com/contact.aspx
**********************************************************************************
PLEASE NOTE: if you need technical support or have any sales or technical question, don't use comments. Instead open a TICKET here: https://www.iperiusbackup.com/contact.aspx
*****************************************