Data encryption in backup operations is one of the most critical features that dedicated software must take into consideration, not only because it is a necessary measure, but also because there are laws to be respected.
Every day, thanks to mobile devices and intensive use of several computer applications, we produce and make use of a large amount of data.
Especially when you talk about sensitive and personal data, proper attention must be paid to protecting them.
Encrypting disks and files helps protect data in the event of incorrectly processed, stolen, lost or disrupted physical machines.
Why is it useful to encrypt backup data?
As you can imagine, making a complete copy of all the data contained on a computer and keeping it in one place is an element of extreme vulnerability.
Data theft or accidental loss could put your company or person at risk. Let’s think, for example, about health data and how much this could mean if they went into the wrong hands.
The GDPR, which entered into force in May 2018, also takes into account the data encryption.
In particular, article 32 contains the guidelines to be followed to guarantee the Security of processing.
The IT techniques related to data encryption must also be followed by a rising awareness of the topic so that appropriate behavioural measures are implemented at all levels to ensure, for example, that the encryption passwords are kept secure
Are online backups secure?
We know that hard drives and all other mass storage devices can decline and become damaged.
It is, therefore, necessary to make periodic copies of our data to be stored in a secure environment, possibly different from the one in which the backup was made.
Here is the cloud backup or on NAS comes to help on this aspect.
When we store our data on online servers, it becomes imperative to protect our data with an encrypted backup.
There are two types of options for encrypting your online backup.
One is based on the host and the other on the client.
In the first case, the data encryption is performed on the host service, while in the second one directly on the client before sending the copy to the server that will keep it.
When it comes to online backups, there is often the fear that our data on remote servers are not correctly stored or that during transfer, these can be intercepted.
Iperiusbackup answers these doubts by providing a client-side encryption feature so that when you distribute them on a cloud service, the data is accurately encrypted.
Encryption algorithms
Cryptography studies and finds the best data encryption and decryption procedures.
The discipline consists of functions that take a plain message in input and return it cyphered on exit by making substitutions or encodings.
To make a complete encryption process, it is also necessary to define the decryption algorithm, the one that performs the reverse job.
There are two types of algorithms:
- symmetrical key
- asymmetric key
In the first case, a single key is the same used both to encrypt and to decrypt data.
In the second case, the encryption and decryption keys are distinct and are better known as public-private keys pairs.
In this type of encryption, the recipient and the sender both know the public key that must be distributed and a private, personal and secret key.
The use of this pair of keys has been introduced to avoid communication of the decryption key to the recipient, as is the case with symmetric key encryption.
One of the two keys is used to code and the other to decode.
The asymmetric key is used, for example, in the digital signature: the message is signed with the sender’s private key and whoever has the sender’s public key can verify its authenticity.
The algorithm that is most widely used in encrypting data and therefore, also in the case of encryption of backup data, is the symmetric key one.
Some algorithms are:
- DES – DataEncryptionStandard (56-bit key)
- 3DES (which uses a key three times the length of DES)
- AES – Advanced Encryption Standard which can use 128, 192 and 256 bit keys.
The latter is a standard used by the US government to protect confidential information: those with a 128-bit key are defined as “secret“, while those with a 192 and 256-bit key are called “top secret“.
Iperiusbackup uses AES-256 encryption.
Note that DES and 3DES were used in the past years, but with the technological evolution of computing potentials, they are now too vulnerable.
How to implement encryption on clients with IperiusBackup?
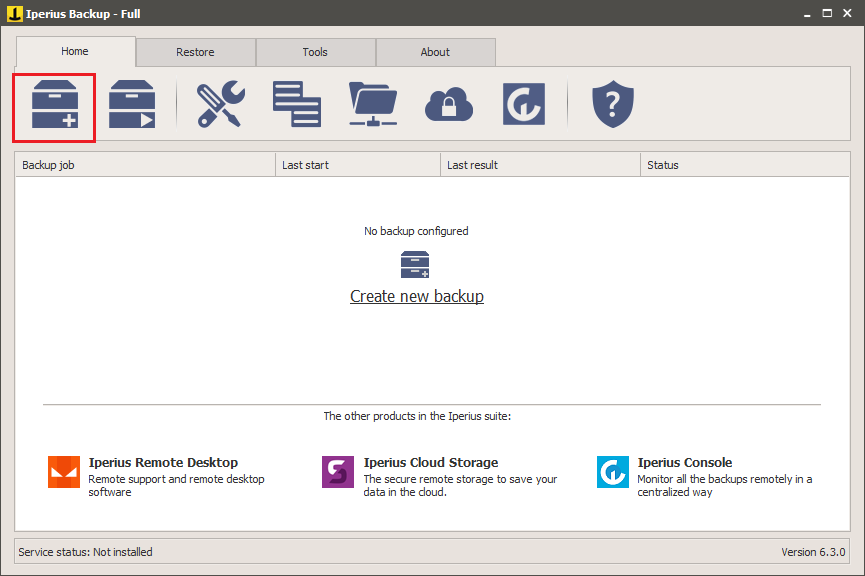
Below we’ll show you the steps to follow to carry out the encryption of your data to obtain a protected backup.
First, let’s create a new backup operation.
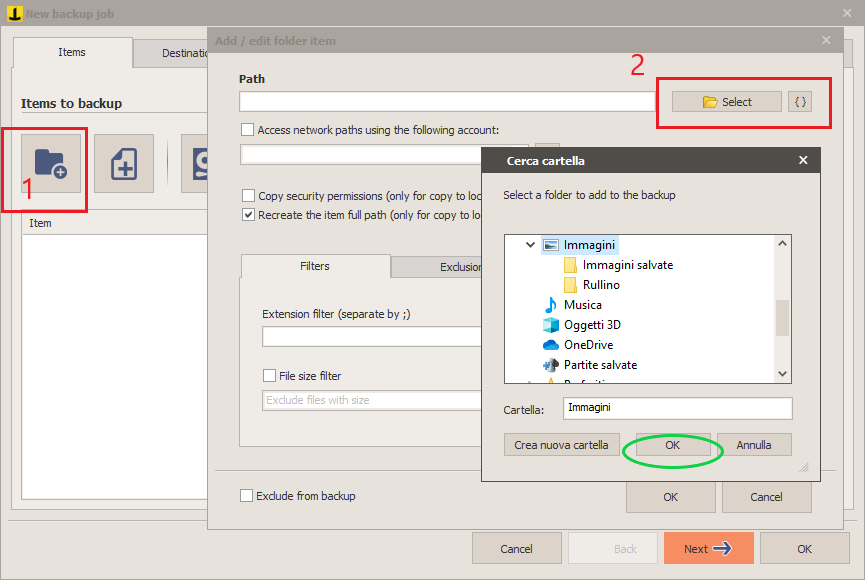
Choose the source folders.
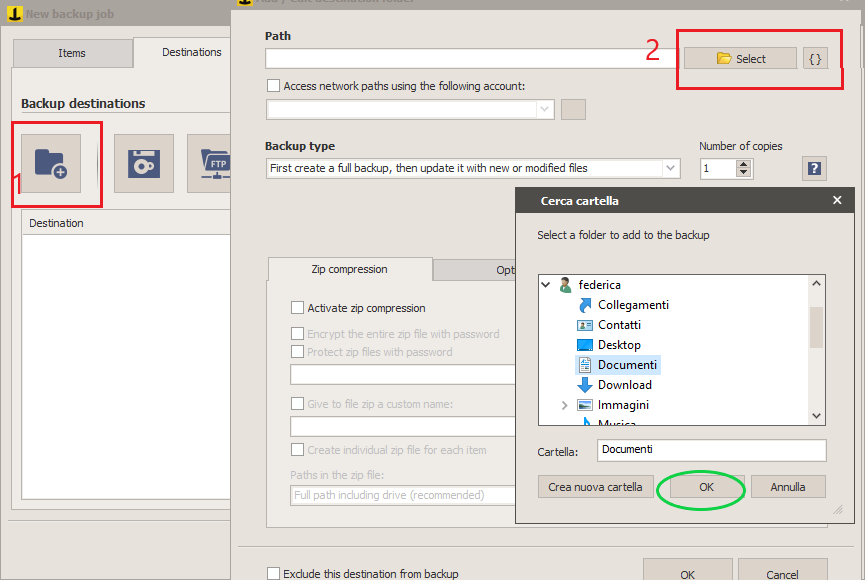
As destination folders, we can choose between:
- a folder on disk;
- Tape destination;
- FTP destination;
- cloud destination.
In our case, we choose a folder on disk.
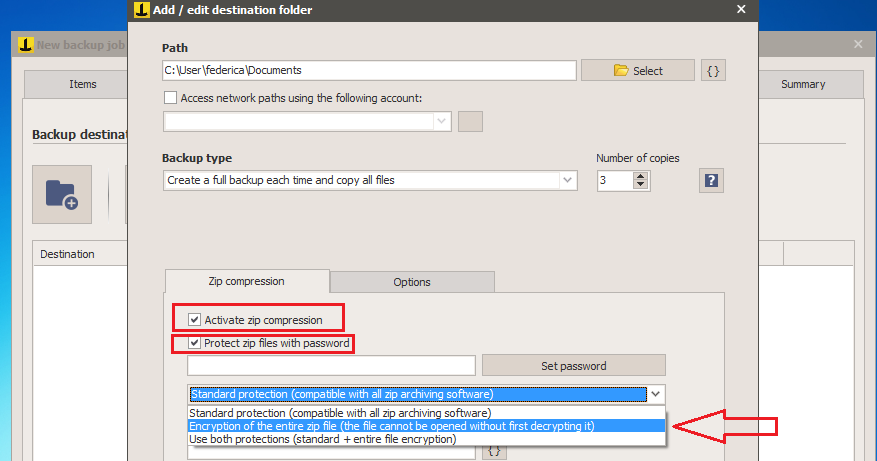
To perform the encryption, after selecting the destination folder, choose the options “Activate zip compression”, “Protect zip file with password” and then choose the encryption type among Standard Protection, Encryption , or both.
Finally, set the password and save.
At this point, it is possible to add some other details, and our backup is ready to be encrypted.
This is just a brief tutorial on encryption of backup data, but IperiusBackup is much more.
To discover all its features, let’s go to the dedicated page.

Hi,
I don’t have the Zip tab for encryption in the paid version? Is this right?
Kind Regards,
Antony
Hi,
you have the encryption option in all the paid version of Iperius Backup, you find it in the Destinations settings inside the Job.
For more technical support, please open a ticket on https://support.iperius.net
When protecting zip files with a password what is the difference between “Standard Protection” and “Encryption of the entire zip file”? Do both forms use AES-256?
Yes, both are AES 256. The encryption of the entire zip file will make it not browsable using other programs, unless you first decrypt it with Iperius. The standard protection will protect the zip with a password, so you can open the zip with WinZip or 7zip and extract the files using that password
Hi,
Is it possible to encrypt or password protect Drive Image backups? I can’t find that option.
regards,
Hi,
yes it’s possible but only if you enable the encryption in the second panel Destinations, so if you add a second destination to the backup, not in the first one.
For more technical support, open a ticket on https://support.iperius.net/
Hi
1) When creating a password by clicking on ‘Set password’, where does this password actually get physically stored? In terms of security, are Iperius staff (or anyone else) ever able to access it?
2) Choosing to backup a folder with Both protections (Standard + Entire File Encryption). When Restoring you only need one password to then ‘unlock’ both. Just a suggestion, but how about 2 passwords for added security? One password for Standard, and another different password for Entire File Encryption.
Hi,
for technical support open a ticket on https://support.iperius.net/