Active Directory is the main core of IT infrastructure of each company in the world and the first layer to build security, compliance, automation for users and computers. To create the right infrastructure, is not necessary to be a wizard but it’s important to know some little tricks to avoid issues with configuration and security.
What is Active Directory?
Active Directory was created over 18 years ago with Windows 2000 Server to consolidate a model introduced in Windows NT4. The idea of AD is to have a database with all the information about users, groups, computers and other items to simplify access to resources. Like a database, the applications and the Windows roles are able to read the properties, the permission and many other details.
An important feature of Active Directory is the possibility to extend the schema to add new columns, properties and values. Some applications, like Exchange Server, use Active Directory to add their components and features to read properties and avoid the need to use different systems.
Before starting with the configuration, it is necessary to learn a couple of terms in regards to Active Directory, because these are part of the model, and knowing them is critical to create the right configuration and understand how to troubleshoot.
Forest
When you create the first Domain Controller, it is necessary to create the Forest name that is also the first Domain Name (ex. contoso.com). The forest name is unique and should not be changed, unless there’s a simple model and there aren’t any changes made by other software like Exchange Server. One forest cannot talk with another forest unless there’s a Trust; this is the method to make a connection between different companies or when there’s a fusion between different infrastructures. The Trust allows systems to read information across domains and assign permissions without creating the objects twice.
Domain
The domain name is the heart of everything. When you build the first Domain Controller, you choose the domain name and that label will be added to every resources of your infrastructure. Changing the domain name is supported unless there’s a complex model or an application that does not support this task, like Exchange Server. To split management, or create a separated logical area, there’s the possibility to create a Child Domain Name (ex. it.contoso.com); each sub domain needs to have a separate Domain Controller and the management is delegated to them. In this case, the trust between main and sub domain is created automatically and this allows reading information across areas.
FSMO
The Flexible Single Master Operation are the 5 roles where the entire AD revolves. When you want to add a new domain controller or synchronize the time or create new items (ex. Groups or Users), one of these roles are called in action. By default the FSMO roles are created in the first DC but can be split to two or three machines (depends on your infrastructure). The 5 roles are:
- Schema Master (Forest)
- Domain Naming Master (Forest)
- Primary Domain Controller (Domain)
- Infrastructure Master (Domain)
- RID (Domain)
If you lose a Domain Controller with one of these roles, some functionalities can be limited. For example, without the Primary Domain Controller the infrastructure is not able to receive password updates when passwords are changed for the computer and for user accounts. For more information about FSMO Roles and how to optimize the placement, check the Microsoft article: FSMO placement and optimization on Active Directory domain controllers.
Global Catalog
A global catalog is a multi-domain catalog that allows faster searching of objects without the need for a domain name. It helps in locating an object from any domain by using its partial, read-only replica stored in a domain controller. As it uses only partial information and a set of attributes that are most commonly used for searching the objects from all domains, even in a large forest, can be represented by a single database of a global catalog server.
A global catalog is created and maintained by the AD DS replication system. The predefined attributes that are copied into a global catalog are known as the Partial Attribute Set. Users are allowed to add or delete the attributes stored in a global catalog and thus change the database schema. The best practice is to add the GC in each Domain Controller of your infrastructure, but in most cases it’s better to avoid this.
DNS
The Domain Name System includes a tree of domain names. DNS assigns domain names and maps the names to IP addresses by designating an authoritative name server for each domain. These servers are responsible for particular domains and can assign the authoritative name servers to subdomains. Without DNS, the entire Active Directory fails and a wrong configuration record can block the communication from servers. From the client side, the DNS resolver is responsible for initiating and sequencing queries that lead to full resolution of the resources sought. These queries are either recursive or nonrecursive.
Each domain controller should have the DNS Role enabled to increase the fault tolerance. When there’s an issue with resolution, it is necessary to check the logs to understand if the replica between Domain Controllers is working properly.
Build Active Directory Infrastructure
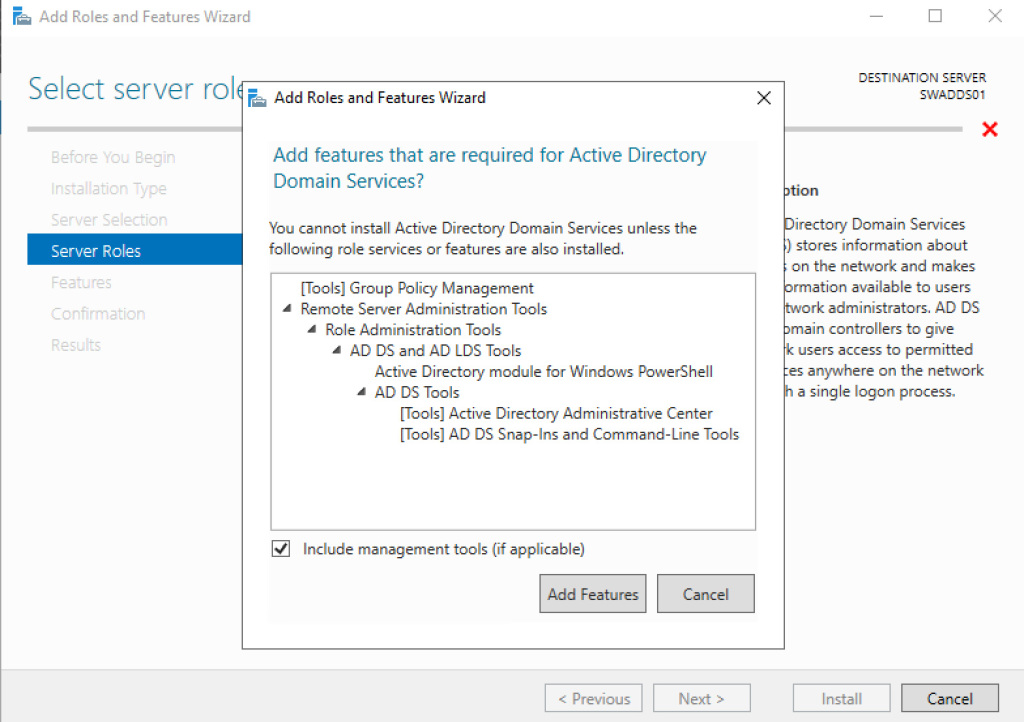
Creating an AD infrastructure is very easy because there’s a great wizard. The first step is to add the roles called Active Directory Domain Services and DNS Server – figure 1.
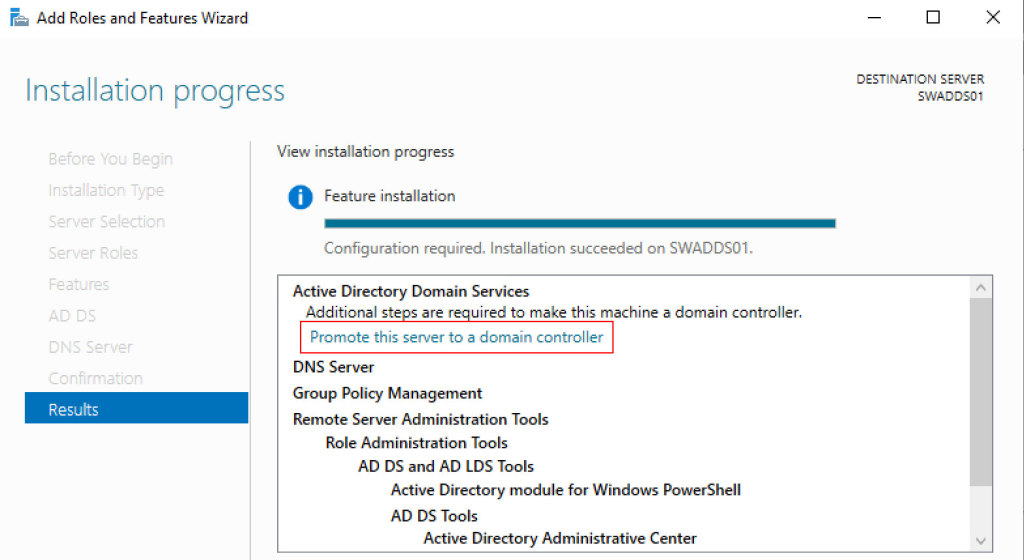
When the installation is finished, we are able to promote the server to be a Domain Controller – figure 2.
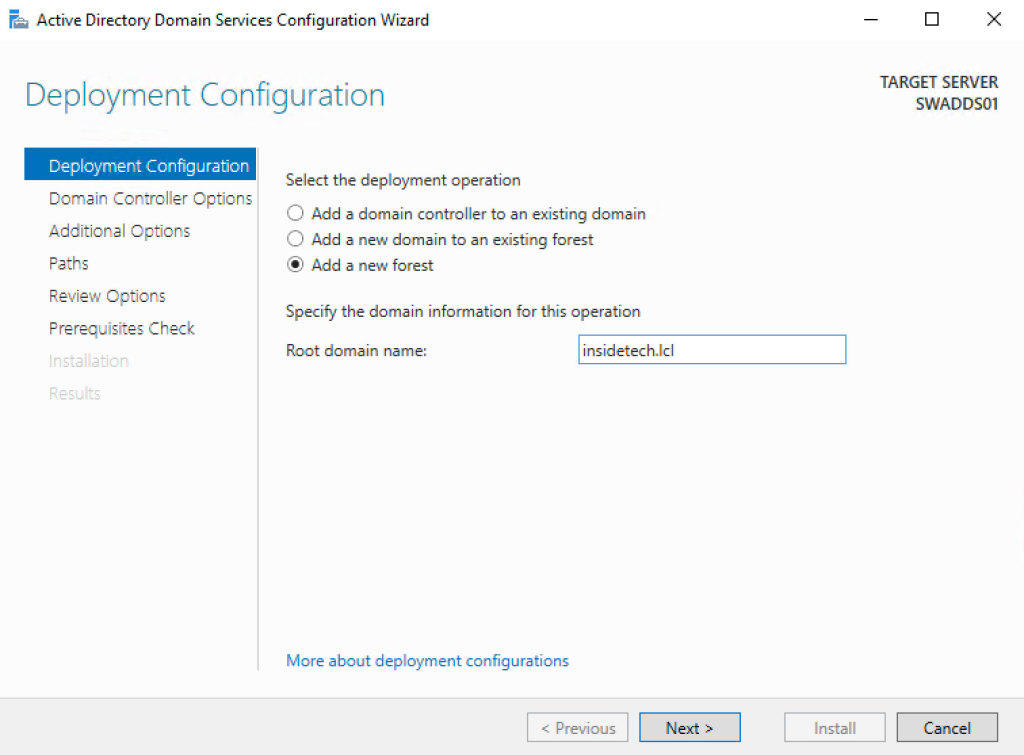
Since Windows Server 2012, the old dcpromo.exe has been deprecated, because there’s a new configuration wizard. Select Add a New Forest – figure 3 – and enter the Root Domain Name.
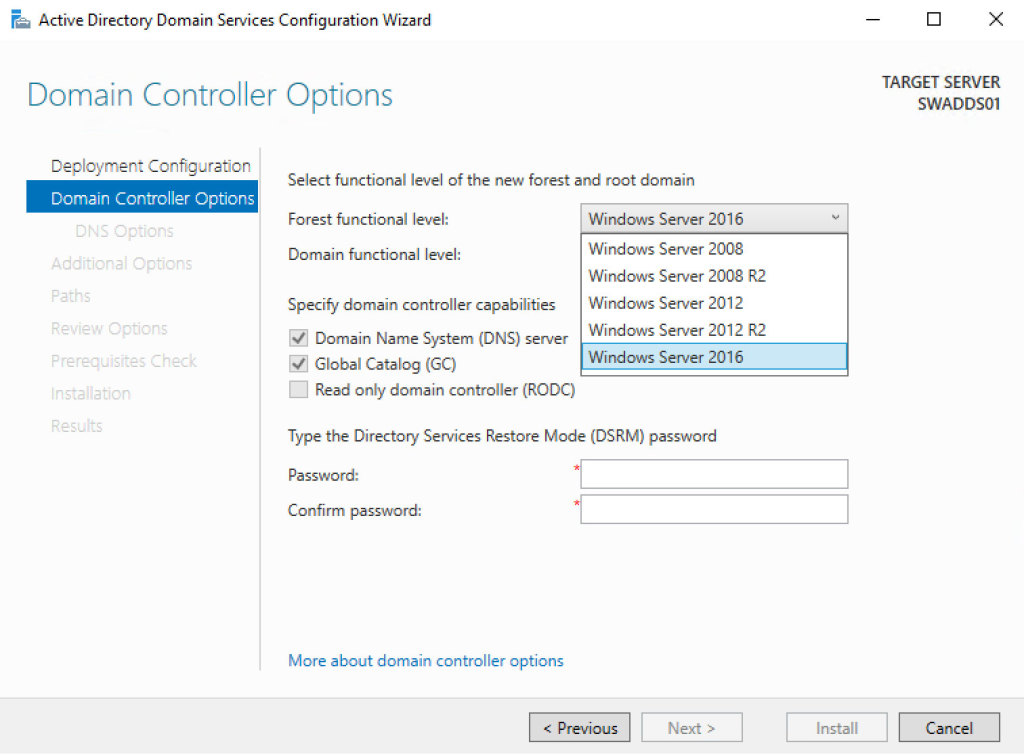
The second step is to select the Forest/Domain Functional Level; this is very important because it cannot be downgraded after the deployment but can be raised. The minimum level should be Windows Server 2012 because Windows Server 2008 and 2008 R2 are near to End-of-Life; don’t forget that some applications, like Exchange Server 2019, requires a level of at least Windows Server 2012 R2. By the way, raising the level is not a problem, is supported in live mode but must be planned in case your infrastructure is complex. The upgrade order is always the same: Forest and later the Domain.
As you can see from the figure 4, the first Domain Controller must have the Global Catalog and DNS role enabled. Enter the Directory Services Restore Mode password and click next.
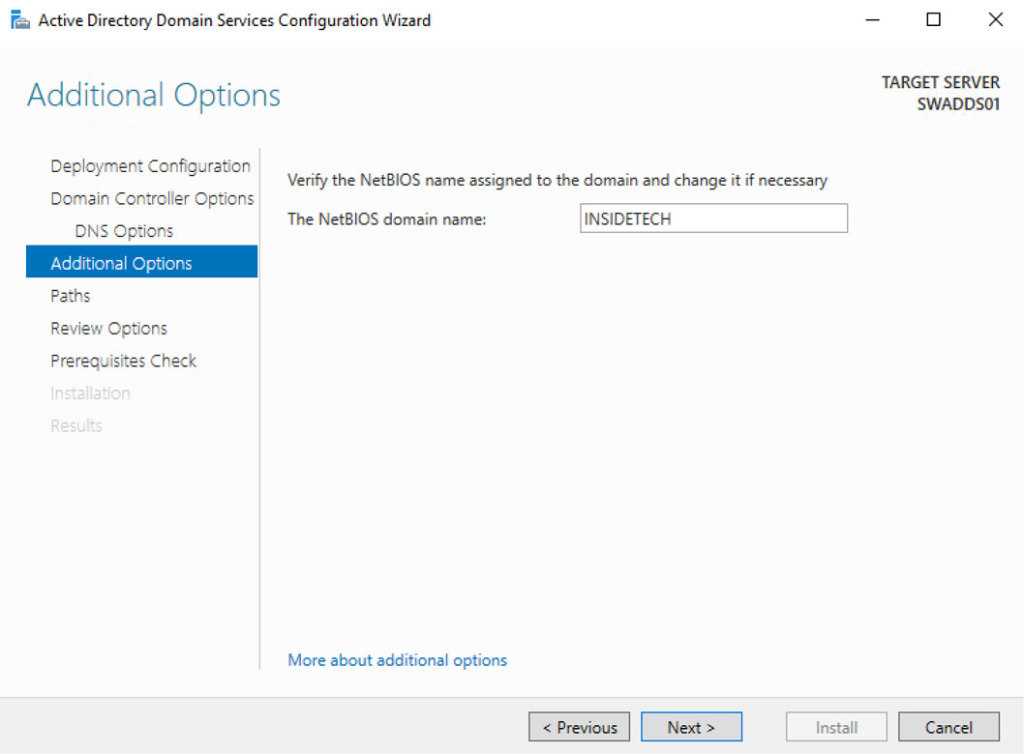
The wizard continues with the NETBIOS name, that should be the same of domain or, in case the domain name is too long, a short version.
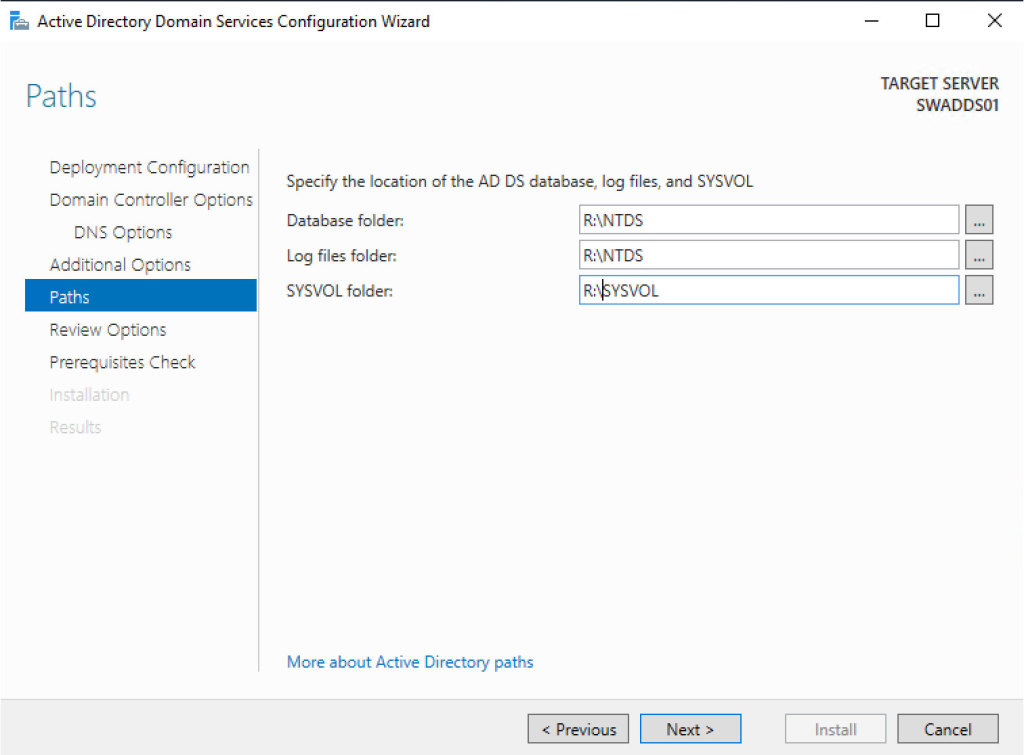
The Path is very important when you create your DC, because it must be configured perfectly. When you use a virtual machine, it could be better to configure another disk (fixed size) with a size of at least 5GB (the size depends on how large is the infrastructure). Format the volume as NTFS and assign a letter; remember that ReFS is not supported. If you plan to install an antivirus, configure the folder exclusion to avoid database corruption. Int theADDS Configuration Wizard, select the new path and go ahead.
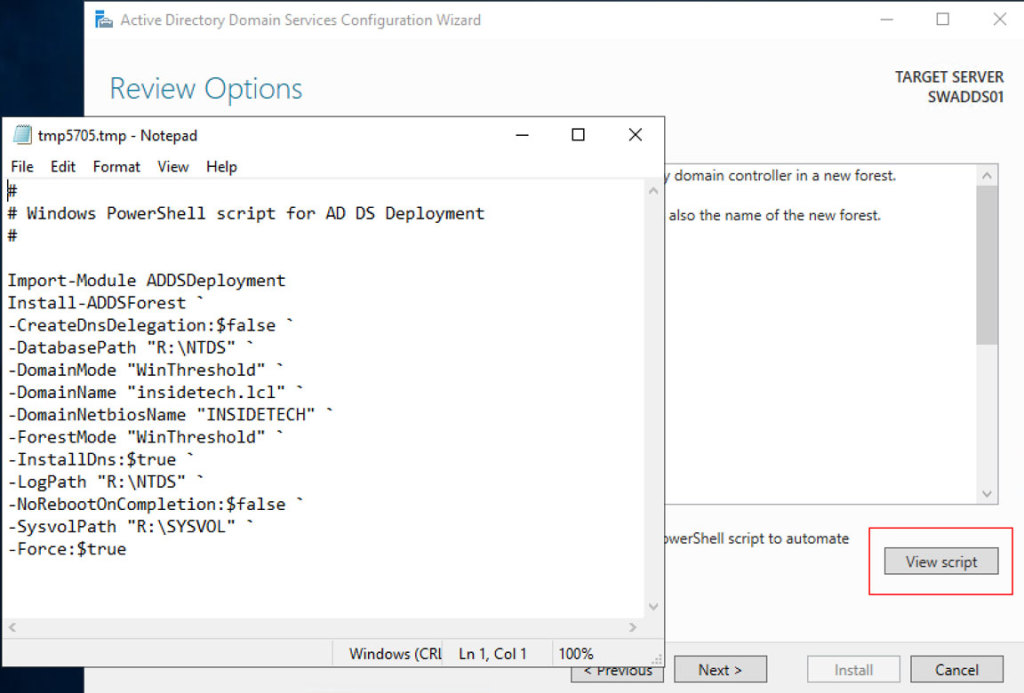
The “Review Options” tab shows the summary of previous steps and give us the possibility to fix potential errors, but allows also to generate the PowerShell script in case want use command line instead GUI.
The “Prerequisites Check” verifies if there’s an issue that can block the configuration. If you are creating the first Domain Controller, all the errors can be skipped. Click on Install button to start the procedure; the execution time can change by the infrastructure and the complexity model. After the reboot, your machine will be ready to be used as Domain Controller.
Best Practice
When you plan to build an Active Directory infrastructure, it is good to know some tricks to avoid security and configuration issues:
Rename Domain Admin – The first user used to start an attack is administrator, so your first step is change the default domain admin name; use a naming completely different from standards, like AdminContosoAD.
Strong Password for Domain Admin – Security, security, security! The Domain Admin must have a strong password and the credentials must be reserved.
Dedicated Credentials for IT – One of first rule is to separate default credentials from management to avoid security escalation in case of external attack.
Assign the Right Permission – If you have multi admins in your infrastructure is fundamental to assign the right permission and credentials for each user. No one should be over Domain Admins to avoid possibility to change the AD Schema or modify the Forest model.
Configure GPO – Configuring Group Policies by Users and Computers, this allows the perfect granularity. Remember to avoid too many GPOs but also to consolidate many settings in one single GPO. Don’t use the Default Domain Policy GPO!
Strong Password for Users – Not only for the Domain Admin, all users must follow the password complexity requirements. If you use Windows 10, one idea is to configure Windows Hello for Business to simplify the authentication method, without reducing security.
Enable Recycle Bin – The Recycle Bin was introduced in Windows Server 2008 R2 and is the perfect way to restore an item in few seconds, without having to run AD Restore.
At Least Two Domain Controller – It does matter if your infrastructure is not an enterprise, you should have two Domain Controller to prevent critical failure.
Remove Obsolete Items – Don’t forget to clean your infrastructure from users and computers where they are no longer present or necessary. This is to avoid issues or security problems.
A Domain Controller is not a Computer – Don’t install anything inside a Domain Controller! No software, no third-part applications, no roles, nothing! A DC must be clean!
Naming Convention Rule – Define a naming convention before build your infrastructure, users, clients, servers, devices and resources (groups, share, more). This will help you to simply management and scalability.
Patch Your DCs – Attackers are quick to exploit known vulnerabilities, this means that you must always keep updated your machine. Plan the right schedule time to install the Windows updates.
Auditing – Deploy an auditing solution to know who make changes. This is not a GDPR requirements but is also a way to prevent security issues.
Best Practice Virtual Machine
There are a couple of rules to bear in mind, when you build a Domain Controller in a virtual machine:
Virtualized DC is Supported – Starting Windows Server 2012, when a new feature called VM Generation-ID was added, is supported install a Domain Controller as virtual machine. Should be used a physical DC? Depends on the infrastructure but for the major of companies the answer is no. What is important, is to configure the Start Action as Always Start in 0 seconds.
Do Not Checkpoint Virtualized – Checkpoints for DC are now supported but could be better to avoid this operation.
Disable Time Synchronization – Domain Controllers expect that they are at the top of the local time hierarchy and leave the Host Time Synchronization Service causes it to override any other source set for the Windows Time service and this could cause issues.
Do Not Place Domain Controllers in Saved State – When a virtual machine resumes from a saved state or is reverted to a checkpoint, the only thing that is guaranteed to fix its clock is the Time Synchronization Service. But, as you know from above, you can’t enable that on virtualized domain controllers. If its clock skews too far, it might never fix itself automatically.
Do Not Convert Domain Controller – It does matter if you have a physical or virtual DC, the convert is wrong and not supported. If you want migrate from VMware to Hyper-V, the Domain Controller must be reinstalled from zero; same thing if you have physical DC.
Upgrade in Place – Like conversion, the upgrade in place is not supported so if you want install a new version of Windows Server, plan to deploy a new machine, add into the AD Forest, move the FSMO roles and demote the oldest Domain Controller. There’s no other way!
Replica – The replica should not be used in the majority of cases. If you have a remote Disaster Recovery site, could be much better configure another Domain Controller and use the AD Replica system because is better.
Consideration
Now you have all the information to configure your Active Directory with the most important best practices to create a great infrastructure and avoid security issues. As usual, read the documentation before starting any kind of activities.


PLEASE NOTE: if you need technical support or have any sales or technical question, don't use comments. Instead open a TICKET here: https://www.iperiusbackup.com/contact.aspx
**********************************************************************************
PLEASE NOTE: if you need technical support or have any sales or technical question, don't use comments. Instead open a TICKET here: https://www.iperiusbackup.com/contact.aspx
*****************************************